Preparing for my F5 Bip-IP certification
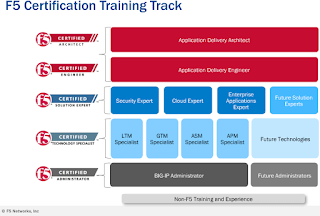
We are implementing a setup of F5 Big-IPs, and I decided its time to get back on the certification tracks. As such, I am going to start with the F5 Certified Bip-IP Administrator certification.
This certification requires 2 exams: Application Delivery Fundamentals, and TMOS Administration. I have been told that the first exam is little more than a “pulse check”, and that if you are familiar with computing and networking concepts, it shouldn’t be a challenge. After looking at the exam description, it doesn’t look too hard, but some study is still suggested.
According the published exam blueprint, the exam is based on v11.4 (11.6 is current as of this writing) and covers the following:
Section 1: OSI
Objective 1.01 Explain, compare, and contrast the OSI layers
- Describe the function of each OSI layer
- Differentiate between the OSI layers
- Describe the purpose of the various address types at different OSI layers
Objective 1.02 Explain protocols and technologies specific to the data link layer
- Explain the purpose of a switch’s forwarding database
- Explain the purpose and functionality of ARP
- Explain the purpose and functionality of MAC addresses
- Explain the purpose and functionality of a broadcast domain
- Explain the purpose and functionality of VLANs
- Explain the purpose and functionality of link aggregation
Objective 1.03 Explain protocols and apply technologies specific to the network layer
- Explain the purpose and functionality of IP addressing and subnetting
- Given an IP address and net mask, determine the network IP and the broadcast IP
- Given a routing table and a destination IP address, identify which routing table entry the destination IP address will match
- Explain the purpose and functionality of Routing protocols
- Explain the purpose of fragmentation
- Given a fragment, identify what information is needed for reassembly
- Explain the purpose of TTL functionality
- Given a packet traversing a topology, document the source/destination IP address/MAC address changes at each hop
Objective 1.04 Explain the features and functionality of protocols and technologies specific to the transport layer
- Compare/Contrast purpose and functionality of MTU and MSS
- Explain the purpose and functionality of TCP
- Explain the purpose and functionality of UDP
- Explain the purpose and functionality of ports in general
- Explain how retransmissions occur
- Explain the purpose and process of a reset
- Describe various TCP options
- Describe a TCP checksum error
- Describe how TCP addresses error correction
- Describe how the flow control process occurs
Objective 1.05 Explain the features and functionality of protocols and technologies specific to the application layer
- Explain the purpose and functionality of HTTP
- Differentiate between HTTP versions
- Interpret HTTP status codes
- Determine an HTTP request method for a given use case
- Explain the purpose and functionality of HTTP keepalives, HTTP headers, DNS, SIP, FTP
- Differentiate between passive and active FTP
- Explain the purpose and functionality of SMTP
- Explain the purpose and functionality of a cookie
- Given a situation in which a client connects to a remote host, explain how the name resolution process occurs
- Explain the purpose and functionality of a URL
Section 2: F5 Solutions and Technology
Objective 2.01 Articulate the role of F5 products
- Explain the purpose, use, and benefits of APM, LTM, ASM, GTM
Objective 2.02 Explain the purpose, use, and advantages of iRules
- Explain the purpose of iRules
- Explain the advantages of iRules
- Given a list of situations, determine which would be appropriate for the use of iRules
Objective 2.03 Explain the purpose, use, and advantages of iApps
- Explain the purpose of iApps
- Explain the advantages of iApps
- Given a list of situations, determine which would be appropriate for the use of iApps
Objective 2.04 Explain the purpose of and use cases for full proxy and packet forwarding/packet based architectures
- Describe a full proxy architecture
- Describe a packet forwarding/packet based architecture
- Given a list of situations, determine which is appropriate for a full proxy architecture
- Given a list of situations, determine which is appropriate for a packet based architecture
Objective 2.05 Explain the advantages and configurations of high availability (HA)
- Explain active/active
- Explain active/standby
- Explain the benefits of deploying BIG-IP devices in a redundant configuration
Section 3: Load Balancing Essentials
Objective 3.01 Discuss the purpose of, use cases for, and key considerations related to load balancing
- Explain the purpose of distribution of load across multiple servers
- Given an environment, determine the appropriate load balancing algorithm that achieves a desired result
- Explain the concept of persistence
Objective 3.02 Differentiate between a client and server
- Given a scenario, identify the client/server
- Explain the role of a client
- Explain the role of a server
Section 4: Security
Objective 4.01 Compare and contrast positive and negative security models
- Describe the concept of a positive security model
- Describe the concept of a negative security model
- Given a list of scenarios, identify which is a positive security model
- Given a list of scenarios, identify which is a negative security model
- Describe the benefits of a positive security model
- Describe the benefits of a negative security model
Objective 4.02 Explain the purpose of cryptographic services
- Describe the purpose of signing
- Describe the purpose of encryption
- Describe the purpose of certificates and the certificate chains
- Distinguish between private/public keys
- Compare and contrast symmetric/asymmetric encryption
Objective 4.03 Describe the purpose and advantages of authentication
- Explain the purpose of authentication
- Explain the advantages of single sign on
- Explain the concepts of multifactor authentication
- Describe the role authentication plays in AAA
Objective 4.04 Describe the purpose, advantages, and use cases of IPsec and SSL VPN
- Explain the purpose, advantages, and challenges associated with IPsec
- Explain the purpose, advantages, and challenges associated with SSL VPN
- Given a list of environments/situations, determine which is appropriate for an IPsec solution
- Given a list of environments/situations, determine which is appropriate for an SSL VPN solution
Section 5: Application Delivery Platforms
Objective 5.01 Describe the purpose, advantages, use cases, and challenges associated with hardware based application delivery platforms and virtual machines
- Explain when a hardware based application deliver platform solution is appropriate
- Explain when a virtual machine solution is appropriate
- Explain the purpose, advantages, and challenges associated with hardware based application deliver platform solutions
- Explain the purpose, advantages, and challenges associated with virtual machines
- Given a list of environments/situations, determine which is appropriate for a hardware based application deliver platform solution
- Given a list of environments/situations, determine which is appropriate for a virtual machine solution
- Explain the advantages of dedicated hardware (SSL card, compression card)
Objective 5.02 Describe the purpose of the various types of advanced acceleration techniques
- Describe the purpose of TCP optimization
- Describe the purpose of HTTP keepalives, caching, compression, and pipelining